
Information technology is growing exponentially with the advent of new technologies in the field which in turn is impacting cyber security. The world...
Read More
Before we get into the ways to increase the speed of the computer we first need to understand what Registry is. A registry is a database used to...
Read More
Web Server Pen-Testing is applied to 3 main areas: identification, analysis, and reporting flaws (e.g., protocol relationship vulnerabilities, configu...
Read More
A VPN (Virtual Private Network) is software that conceals your identity while accessing the internet and encrypts your activity. VPNs give you an addi...
Read More
In the digital era, defining the crucial role of the internet in everyone’s life is not as easy as you might think. In spite of this positive as...
Read More
VPN stands for “Virtual Private Network,” and when used correctly, it typically provides a service for safe internet surfing.
It...

In the year 2013, a Harvard student made efforts to evade final examinations. For this, he made a plan to send an anonymous bomb threat. One of the in...
Read More
Software as a Service (SaaS) security pertains to the measures and practices implemented to safeguard the data, applications, and infrastructure of Sa...
Read More-
 Framework for the Roadmap to cybersecurity
Framework for the Roadmap to cybersecurityInformation technology is growing exponentially with the advent of new technologies in the field whi...
January 19, 2024 -
 5 Little tweaks you can do with Registry to optimize the speed of your system
5 Little tweaks you can do with Registry to optimize the speed of your system Before we get into the ways to increase the speed of the computer we first need to understand...
January 18, 2024 -
 Web Server Penetration Testing Checklist – 2024
Web Server Penetration Testing Checklist – 2024Web Server Pen-Testing is applied to 3 main areas: identification, analysis, and reporting flaws (e....
January 17, 2024 -
 The Top 10 VPN Software for 2024
The Top 10 VPN Software for 2024A VPN (Virtual Private Network) is software that conceals your identity while accessing the internet...
January 16, 2024 -
 8 Best Practices For The Security Of Your Online Identity
8 Best Practices For The Security Of Your Online IdentityIn the digital era, defining the crucial role of the internet in everyone’s life is not as eas...
January 16, 2024 -
 VPNs: Everything you need to know
VPNs: Everything you need to knowVPN stands for “Virtual Private Network,” and when used correctly, it typically provides...
January 12, 2024 -
 Strategies for Countering Tor & Thwart Attacker Anonymity
Strategies for Countering Tor & Thwart Attacker AnonymityIn the year 2013, a Harvard student made efforts to evade final examinations. For this, he made a pl...
January 10, 2024 -
 The top 10 checklists for SaaS Security in 2024
The top 10 checklists for SaaS Security in 2024Software as a Service (SaaS) security pertains to the measures and practices implemented to safeguar...
January 10, 2024 -
 Protecting yourself on vacation is easy with these 6 tips
Protecting yourself on vacation is easy with these 6 tipsThis time, vacationers are targeted by identity thieves, but here's how to completely avoid them...
January 9, 2024 -
 The Top 11 High-Tech Endpoint Security Tools in 2024
The Top 11 High-Tech Endpoint Security Tools in 2024Tools for endpoint security are essential components of cybersecurity because they protect PCs, phon...
January 9, 2024 -
 Is It Worth Using TTB Antivirus Solution To Defend Digital Life?
Is It Worth Using TTB Antivirus Solution To Defend Digital Life?Nowadays, operating systems are advancing very rapidly. As a result, viruses & cyber threats are...
January 5, 2024 -
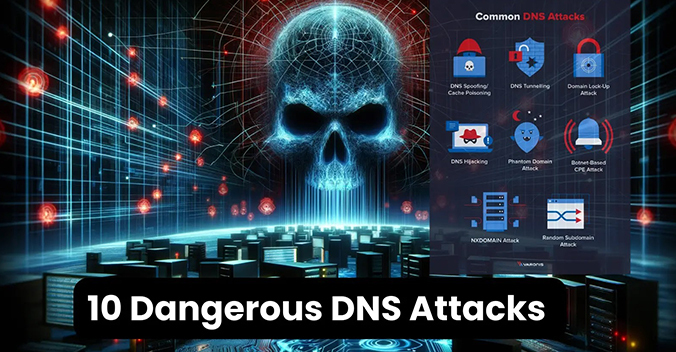 Top 10 Most Dangerous Types of DNS Attacks in 2024 and Their Prevention Measures
Top 10 Most Dangerous Types of DNS Attacks in 2024 and Their Prevention MeasuresThis blog post focuses on proactive cyber defense mechanisms for the top 10 DNS attacks in 2024. It...
January 5, 2024 -
.jpg) Unmasking Spoofing & Sniffing In 2024
Unmasking Spoofing & Sniffing In 2024Introduction
January 3, 2024
In the present digital era, there are so many digital threats that are posing signif... -
 The Top 10 Most Harmful Injection Attacks in 2024
The Top 10 Most Harmful Injection Attacks in 2024Being in any industry, particularly in the network and admin team, means that you need to be aware o...
January 2, 2024 -
 Emerging top 10 cyber security trends in 2024
Emerging top 10 cyber security trends in 2024Nowadays, technology advances to the next level and eases our life. Likewise, as the tech era amplif...
December 30, 2023 -
 An Approach Of AI In A New Age Of Cybersecurity
An Approach Of AI In A New Age Of CybersecurityWith technological advancement, Cyber crimes are not merely increasing but also getting much more co...
December 26, 2023